VPN (Virtual Private Network)
Our increasingly interconnected world offers many possibilities for optimising business processes. More and more companies use the internet to interlink their various offices and locations, integrate partners into their own IT infrastructure, or enable home office or remote access to the workplace. Yet companies should be aware that any of these implementations can cause a security breach. In order to make transferring sensitive data possible, a host of different communication technologies are used. A common solution is in the form of a VPN.
What is a VPN?
A virtual private network (VPN) is a kind of virtual communication network that operates on the basis of a physical network. Generally, the internet is the most commonly used transport medium for VPNs. In order to ensure that data remains safe when transferred through a public cable, transport channels are secured through encryption and authentication methods. Given that data transferred via a VPN is not accessible to participants of the public network it runs on, the term “tunneling” is often used to describe this process. Following this, a VPN makes it possible to transport sensitive data via untrustworthy connections. As a result, it presents an affordable alternative to private cables.
Application areas of Virtual Private Networks
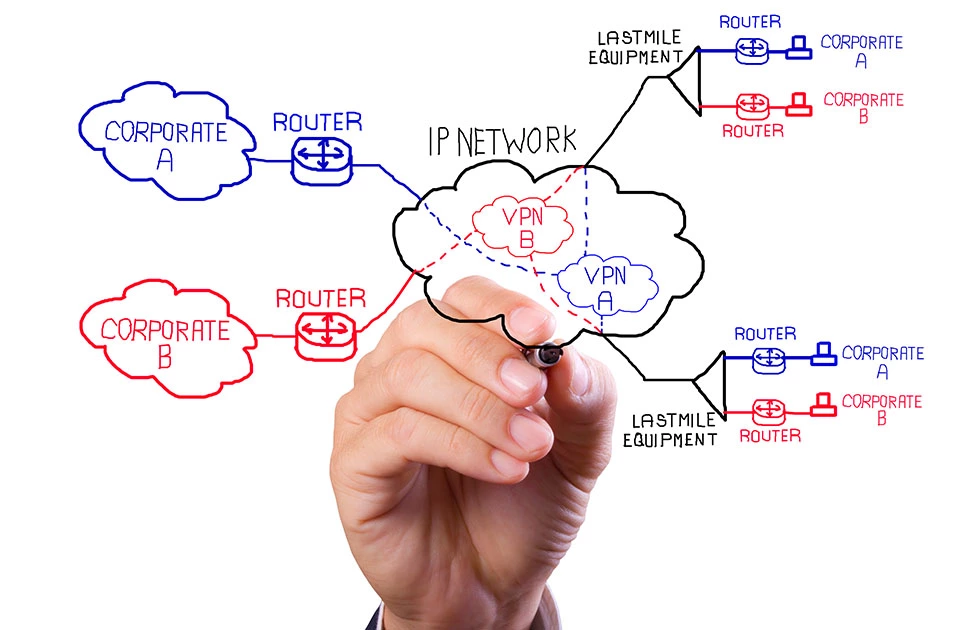
Generally, VPNs are used for one of the following three main reasons: to interconnect two or more company locations via a public network (site-to-site VPN), to remotely access the company network when traveling or from home (end-to-site VPN), or to remotely access one computer from another computer (end-to-end VPN).
Site-to-Site VPN
A site-to-site VPN is used when multiple local networks are to be connected to a virtual communication network, via a public transport medium. Such scenarios are possible, for example, when connecting different company locations with one another. Alternatively, location networks can also be realized, in the form of a corporate network. Corporate networks are based on a private fixed connection, but companies have to rent the corresponding infrastructure first in order to use it. A connection via VPN, on the other hand, relies on a public network. Here an internet connection is the only cost involved. Creating a site-to-site VPN also requires a VPN router; these are needed to build the connection between the VPN tunnel and the local network. Other terms used to describe a site-to-site VPN include: LAN-to-LAN or Branch-Office VPNs.
End-to-Site-VPN
Companies tend to use end-to-end VPNs whenever their networks are to be made available for mobile users working in the field or from their home offices. The tunnel to the local network is created through a VPN client on the external employee’s terminal device; here the main transport medium is also the internet. This enables employees to access the company network (and so any file and mail server located within this) simply via internet connection. An end-to-site VPN is also referred to as a remote-access VPN.
End-to-End VPN
And end-to-end VPN occurs if setting up a network with remote access isn’t possible, and can only be done by connecting one computer to another one. Working on a remote desktop would be a classic use case for this kind of VPN connection. Here, a software program is executed on one computer, and displayed and used on another one. The transport medium for such applications can be the internet or a local company network. For business-related purposes, remote desktop VPNs are used when an employee seeks to access their work computer from home.
Implementing a virtual private network
Many different protocols are used when implementing an encrypted connection via VPN. The most common solutions rely on IPSec, L2TP over IPSec, and SSL.
VPN with IPsec
‘Internet protocol security’ (IPSec) is a protocol suite designed for the internet protocol (IP) with version 6 (IPv6) and enables secure communication via non-trustworthy IP networks. Encryption and authentication mechanisms help ensure that the data traffic’s privacy, authenticity, and integrity are safeguarded. IPSec was developed with IPv6 and was retroactively specified for IPv4.
L2TP over IPSec
A VPN implemented with LTOP over IPSec uses the ‘Layer 2 Tunneling Protocol’ (L2TP). L2TP alone doesn’t contain any encryption. For this reason, the protocol is normally combined with IPSec. While IPSec is only able to tunnel IP packets, L2TP supports a variety of packet-transferring protocols. The combination L2TP over IPSec combines the strengths of both standards. The result is a highly secure and flexible tunneling protocol.
SSL-VPN
SSL was originally developed for use within HTTP environments. This is why the encryption protocol is used for securing VPN connections. Open VPN is a popular software solution for setting up a virtual private network.