Token ring – IEEE 802.5
A token ring is an outdated form of network technology, and today Ethernet is the most prevalent type of wired LAN connection. But that doesn't make the old technology any less interesting. Older methods, now confined to the realms of history, can also help us understand modern networks and why technology has developed as it has.
However, a token ring is not really a ring network, also referred to as a ring topology, even if the name suggests this. In fact, the only ring created is a logical one, not a physical one. We will explain the differences below.
The foundation of a token ring is the IEEE 802.5 network of the “Institute of Electrical and Electronics Engineers” from 1985, in which all participants of the “Local Area Network” (LAN) are connected to form a logical ring. Usually token ring topologies have a transmission speed of 4 or 16 Mbit/s, but in theory speeds of 100 Mbit/s or 1 Gbit/s are also possible.
History of the token ring
Even before the introduction of the token ring, there were, of course, other computer networks. These were not available to the public, like ARPANET, but were mostly developed and used by individual institutions for their own purposes and were therefore not standardised. In the early 1980s, the companies Procom, Apollo Computer, and Proteon were the first to offer token ring networks on a larger scale. IBM then took the matter up and launched its own product in the middle of the decade.
Due to how widespread IBM PCs became, the token ring also began to quickly take over the tech market – and was directly slowed down again. Ethernet technology, which was already developed in the 1970s, also gained more and more popularity in the 1980s, partly thanks to the support of Intel and Xerox. Ethernet beat the competition between the two technologies by introducing low-cost, thin co-axial cables. IBM had charged such high fees for the license of the token ring process that no inexpensive products could come onto the market.
While IBM initially tried to convince the public of the advantages of a token ring, they gave up at the end of the 1990s: Although the IEEE had approved models with 100 Mbit/s and 1,000 Mbit/s, the former was marketed only slightly, and with the latter not a single product made it onto the market.
What is a token ring?
The question of what a token ring network is easier to answer if you know what it is not: a ring topology. A ring topology in the physical sense consists of a circular arrangement of computers. Each net participant is connected to its neighbours to the left and right, so that the network is a closed ring. As soon as a computer within the LAN fails or a connection is otherwise disconnected, the whole network breaks down, and the connection is lost. If another computer wants to participate in the network, the LAN must be interrupted for at least a short moment.
A token ring typology
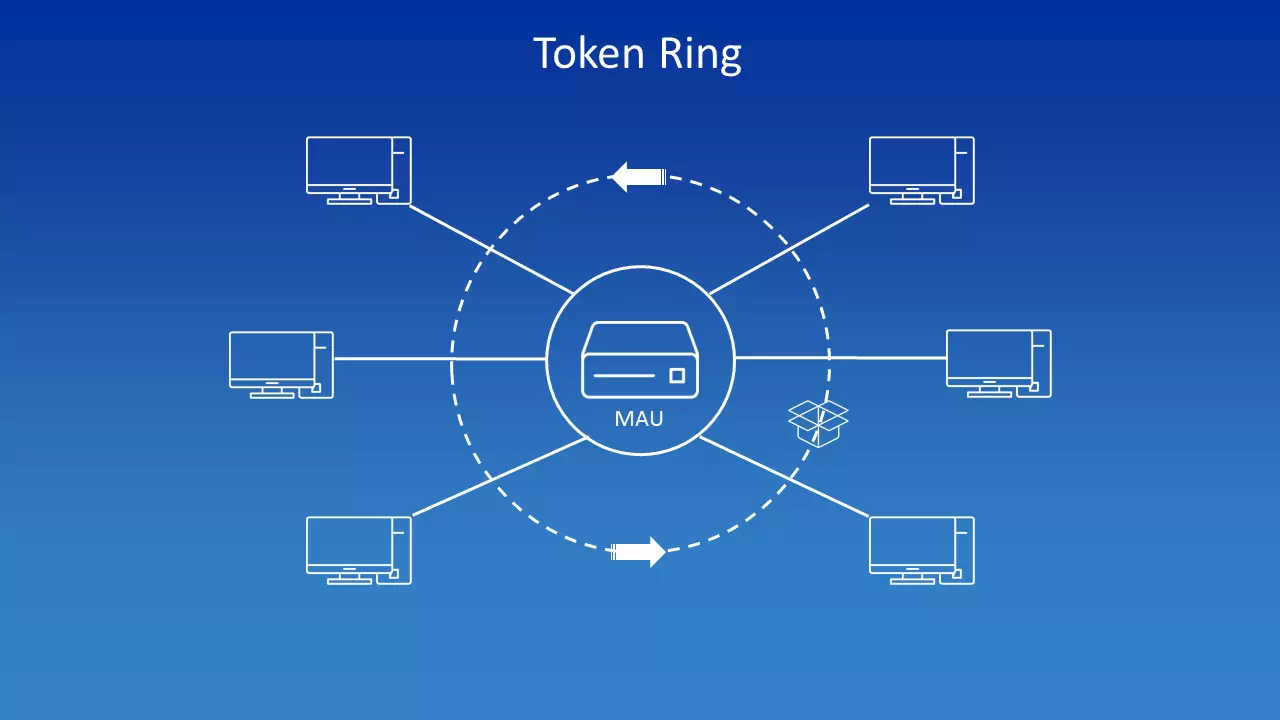
A token ring works somewhat differently to other ring topologies, which is why it’s said that this technology is based only logically on a ring topology. The token ring topology uses Multistation Access Units (MAUs), which allow a star-shaped connection of the connections involved. The distributor is a node that is connected to all computers on the network. There is no direct connection between the individual computers.
Nevertheless there is still a logical ring involved, which is due to the physical star structure, because the data transmission takes the form of a ring – on an abstract level. Although the data is repeatedly transported to the MAU, it is not sent from there to a specified subscriber, but simply to the next computer in the fixed sequence.
Token passing
To avoid chaos, the token passing procedure is used. This method ensures that not all participants send data to the network at the same time. Only computers that are currently in possession of the token have the right to send data packets to the network. This token is passed on in a ring – even if no participant requires a transmission permit, the token continues to circulate. A token is an empty frame of 3 bytes in size, each byte having a separate task:
- Third byte – start delimiter (SD): The first 8 bits of the frame indicate the beginning of the token. The structure is based on the differential Manchester code, which allows a clear assignment.
- Second byte – access control (AC): The access control contains the token bit. If this is set to 0, the token is free, 1 indicates that it is busy.
- First byte – end delimiter (ED): The design of the end delimiter is similar to the start delimiter and makes it clear that the frame is complete.
If a participant receives the frame and does not want to send any information, they simply pass it on to the next in the row. However, if the computer wants to send something, it changes the token bit and attaches the data package to the token. Part of this frame is now also the sender and recipient address. However, the data packet does not immediately reach the receiver, but – via the MAU – is forwarded from participant A to participant B, to C, and so on, for example, until it reaches the correct station. To ensure that the signal does not lose strength on the move, each participant acts as a replicator: it reads in the packet, regenerates it, and sends it back into the ring.
The target station then copies the information, receives the data, and acknowledges this by changing the frame status (FS), the last byte in the whole frame, and transmits the packet. When the data package reaches its original sender again, it deletes the data and releases the token bit again. A token holding time is implemented so that all participants have the chance to transmit data. This time specifies how long a station may take the token for itself.
It doesn't matter whether the data is sent clockwise or counter-clockwise as long as all stations are sending in the same direction.
Possible errors with token rings
Issues can occur in any network, and in most there is the risk that some would cause the network to break down. In a token ring, all computers are standby monitors (SM) by default, but you usually check on the network in the role of an active monitor (AM). Each station can take on this role. The decision as to which station will become AM – and so also which ones remain as SM – is made by a fixed procedure: monitor contention, also called token claiming. The procedure is initiated when a station has determined that the current AM no longer transmits the mandatory active monitor present frame via the ring.
When this happens, the protocol requires a choice for a new active monitor: The first station that has noticed the malfunction of the AM begins to send a so-called claim token frame. The next station in the ring compares the sender's MAC address with its own. If the address of this second network subscriber has a higher value, it replaces the frame with its own. At the end only one station remains: If its frame has circled the ring three times without any other station intervening, a new active monitor is determined.
The active monitor is responsible for the smooth running of the token ring, but standby monitors can also intervene in some cases. In the following scenarios, the token ring network can heal itself:
Token gets lost
As soon as a token passes the active monitor, it sets a timer. If the time span (10 milliseconds) has elapsed before the token reaches it again, the AM detects a problem in the network and generates a new, free token.
Package cannot find a recipient
If one station sends a packet and the recipient station would fail at this very moment, the packet would circle endlessly on the ring, since no station identifies itself as the recipient. When the packet passes the AM for the first time, it converts a specific bit. If the packet passes the AM again, he recognises from the bit that the packet has not reached his recipient. Only the AM can set the bit to 1 and determines that it must already have come into contact with the packet. The active monitor destroys the package and creates a new, free token.
Faulty interfaces
In a normal ring topology, the failure of a station or connection means the complete failure of the network. With a token ring topology, however, the MAU can simply bridge the interface. Faulty stations are detected by a direct neighbour: To do this, the participant located directly behind the damaged computer sends test frames to the neighbour. All other stations enter a waiting mode: no station sends data. If the faulty node detects that its neighbour has submitted a complaint, it starts an error analysis and takes itself off the network.
However, the error can also be at the original station: The fact that the computer can no longer access data may also be due to a faulty network card. So, the participant sets a timer that would give the neighbour enough time to perform a self-test. If no frame arrives after the expiration of the timer, the station assumes an error and starts a test.
The faulty station – if it was not the AM – is simply bypassed during transmission until a solution has been found. If it is the AM, the token claiming starts. When everything works again, the AM creates a new token and mains operation can continue normally.
Pros and cons of token rings
The advantages and disadvantages of a token ring can be seen in a comparison with Ethernet systems. The fact that collisions cannot occur makes the token ring an interesting concept: In a (half-duplex) Ethernet network, collisions caused by several stations transmitting at once are likely. With the help of CSMA/CD you can control how these collisions are handled, but they reduce the speed anyway. In a token ring, however, collisions cannot occur. The token-passing procedure prevents several stations from transmitting simultaneously.
This compensates for the token ring’s lack of speed. While token ring technology was stopped in its development at 16 Mbit/s, Ethernet networks with 100 Mbit/s already existed at that time. If you compare a simple ring topology with the token ring via MAUs, the latter has the advantage of flexible nodes. Adding or removing individual computers from the network is no problem. Even if individual stations fail unexpectedly, the network is not endangered. This in combination with effective troubleshooting makes a token ring a very stable system.
| Pros | Cons |
|---|---|
| No collisions | Old technology |
| Internal error detection and correction | Slow |
| Stations can be easily added and removed | Expensive hardware |