Kata Containers: basics, function, and applications
Kata Containers is a project by an independent, open-source community that works together to combine the advantages of a container system with those of a simple virtual machine.
We explain who’s behind the project and how Kata containers work. Plus, we’ll show you the advantages and disadvantages and the most popular application scenarios for the secure container runtime.
What are Kata Containers?
Kata Containers – a project launched in December 2017 – aims to develop the most lightweight virtual machine possible that works with the same “look and feel” of a container. Kata containers are, therefore, easy to use, highly compatible, and can handle a high workload. What’s more, they still offer a high standard of security. Here, the community utilises stronger isolation externally and a hardware virtualisation technology internally, as a second line of defence.
The Kata Containers project is financed and managed by the OpenStack Foundation (OSF), which is committed to the development and introduction of open infrastructure for cloud computing. For this reason, the OSF code of conduct is a key point of reference for the joint work of the open-source community. The project code is hosted on GitHub – under the Apache 2 license. Large, major companies like Google and Microsoft sit on the Kata architecture committee.
The OpenStack Foundation has provided an in-depth introduction to Kata Containers in the following 30-minute YouTube video:
How do Kata Containers work?
What exactly do the architecture and functionality of Kata Containers look like? To answer this question, we need to look back to the start of the project. In December 2017, the community successfully combined and scaled the best parts of Intel Clear Containers (an Intel project for secure Linux containers) with Hyper runV (a Hypervisor-based runtime for open container initiative projects). In other words, the performance of Intel meets the platform independence of Hyper.
One of the most important aspects in any container system is security. Since containers can be stacked or layered on top of each other, security is often extremely difficult to ensure. Both Intel and Hyper, therefore, aim to achieve high flexibility in a container environment – with similar results, albeit through different means. The simple layering of container formats like Kubernetes on OpenStack or vice versa is just as possible as complex layering of Kubernetes on OpenStack on Kubernetes. This flexibility in creating the desired architecture simplifies the use of Kata containers considerably, without having to forego security.
With Kata, you can implement both an VM isolation on the container level and container isolation through hardware virtualisation. In the case of Kubernetes, VM isolation is not provided to the container level but to the Podman or pods level, because Kubernetes uses the term “pods” instead of “containers”. But this guide will continue to refer to “containers” for reasons of simplicity.
Setting up and executing container systems can be really complex, since many containers typically have to be provided to different computers. With Managed Kubernetes by IONOS, you can plan, organize, and provide your containers more easily – and also scale them freely as required!
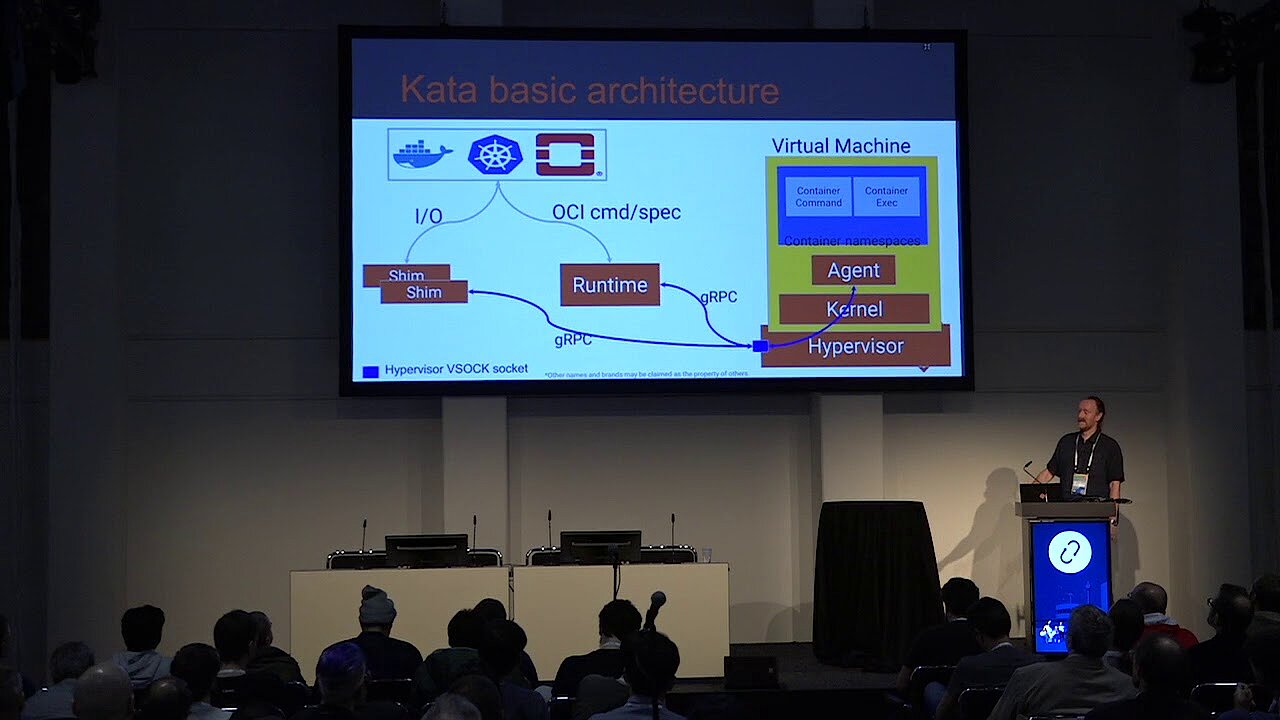
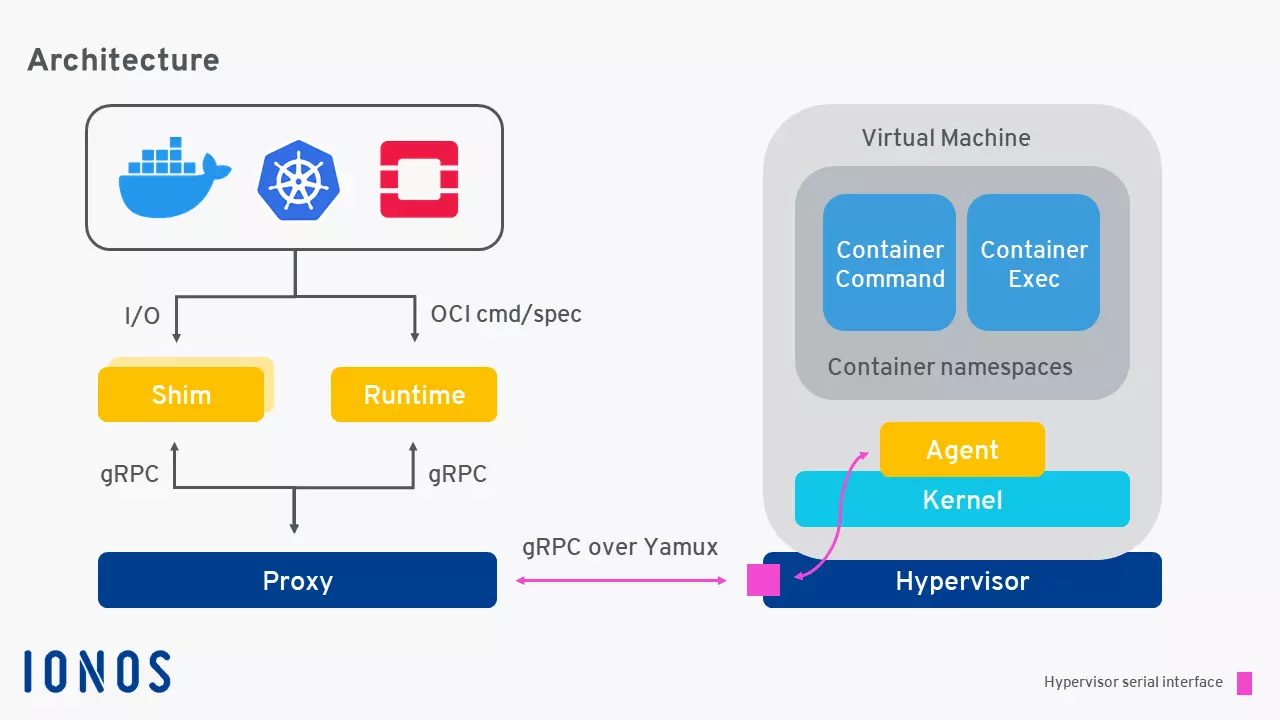
Kata Containers: architecture
The community follows the approach of maximum simplicity and also demonstrates this in the architecture of Kata containers, which generally provides for the following six components:
- Agent
- Runtime
- Proxy
- Shim (compatibility extension for the respective application)
- Kernel (operating system kernel)
- Bundle with QEMU 2.9 (free virtualisation software)
These properties make Kata independent, highly compatible, and highly secure. Besides x86_64, the architecture can also support AMD64, ARM, and IBM p System, and IBM z System. Moreover, Kata Containers allows the use of multiple Hypervisors like QEMU, NEMU, and Firecracker. Integration into the containerd project is also possible.
Compatibility of Kata Containers
Kata 1.10 is compatible with the Docker Community Edition, but also supports all other industry standards such as the OCI container format, Kubernetes CRI interfaces and some older virtualisation technologies, including CRI-O (1.10 commit 393429 or CRI Containerd version 1.0.0) or OCI Runtime Specification (v1.0.0-rc5).
The supported operating systems that run on Kata containers include:
- CentOS (7)
- Debian (9, 10)
- Fedora (28, 29, 30)
- Ubuntu (16.04, 18.04)
- Red Hat Enterprise Linux (7)
- OpenSUSE (Leap, Tumbleweed)
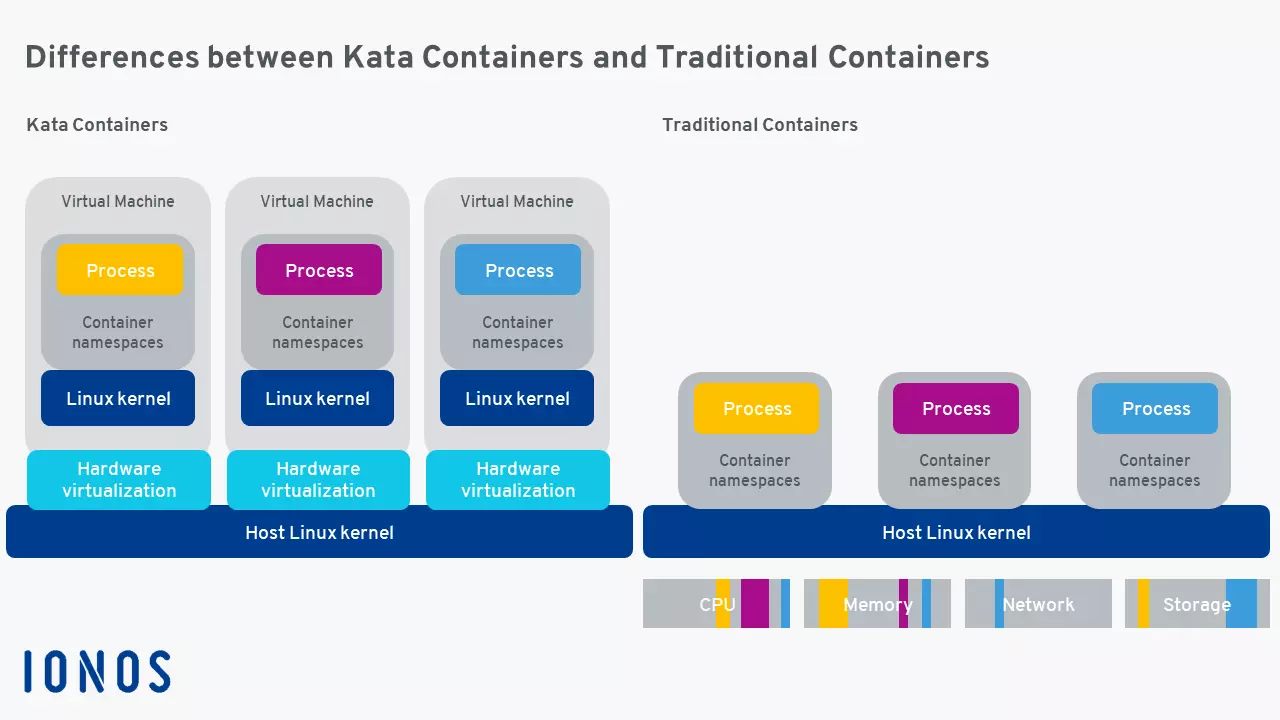
Difference between Kata Containers and conventional containers
The greatest advantage of Kata containers is the combination of simplicity and performance. Nesting containers in full-fledged virtual machines is no longer necessary. The community has instead opted for standard interfaces that simplify entry and connection enormously. Performance remains consistent with a standard Linux container, but does not have the normal performance control of a virtual standard machine thanks to the increased isolation. The following graphic illustrates this beneficial structure:
As a result, the open-source project has already achieved the goal of an open-source container environment, whose components act like containers but offer the performance and security of VMs. Kata Containers has, therefore, been able to resolve the old concerns about containers, such as scaling.
Security of Kata Containers
Conventional containers are light, fast, and are easy to integrate. On the other hand, they come with security risks – especially when they are found on a single operating system. When the containers share a kernel, an I/O path, the same network and memory, it’s enough to simply attack one container in order to jeopardise all others at the same time.
The situation is entirely different with Kata containers: The virtual machines run in a dedicated kernel (operating system kernel), which separates the processes from both the network and E/A, as well as from the memory. In addition to strong isolation, isolation improved with hardware can be used with virtualisation VT extensions.
Kata Containers: overview of advantages and disadvantages
There are many arguments in favour of the ambitious open-source project from the OpenStack Foundation. Even Clear Linux (Intel) has moved away from its proprietary container technology and already supports Kata containers with great success. The key reasons include:
- Excellent compatibility
- Simplicity of use
- High performance
- High security standard
Another advantage is the low energy consumption, even with high performance.
However, Kata is not a distribution for any and all purposes. It’s a special system with some principle limitations. These include operations that are not allowed by a virtual machine, and restrictions that are to be resolved in future updates. An extensive list of the limitations is provided by the community in the official documentation on GitHub. Moreover, Kata containers currently can only be used on Linux distributions.
Another, not insignificant disadvantage is that Kata is still a nascent development. Nonetheless, the technical foundations are promising and are already used across many areas.
Where are Kata Containers used?
As previously mentioned, the community observes the OSF code of conduct. This also encompasses an open management of the entire project and the source code in particular. This openness is best provided by the combination of the two integrated and virtualised, open-source code bases. Its many supports include Kubernetes, Docker, OCI, CRI, CNI, QEMU, KVM, and OpenStack.
Clear Containers and runV – the technical foundations of Kata Containers – are used by major companies around the world, such as JD.com, one of the highest-revenue online stores in China.
Kata containers generally work best where containers are needed that are not to be run on a single kernel. This includes areas of application like continuous integration and provision (CI/CD), edge computing, virtualised network functions, and containers as a service (CaaS). Kata is also perfectly suited to niche implementations. After all, no other container is as simple, efficient, secure, and flexible.