How to Set Up an FTP Server in Ubuntu
In 1985, the transfer protocol FTP (File Transfer Protocol), based on TCP/IP, was established and specified in RFC 959 to make it possible to store files on a server and retrieve them later. The protocol, located on the application layer, makes it possible to transport data via port 20 (client) and 21 (server), as well as create, edit, and read directories. To use this client-server structure, users only need an FTP client and to log-in to a special user account on the server. Secured FTP enjoys a high level of popularity, particularly in webhosting: With the help of the transport protocol and the matching client software, the contents of custom projects are easily uploaded into the web space, creating directory structures. If you host your website with a provider, a corresponding server application, including the required access data, is usually provided. If web hosting and file transfer remain your responsibility, it’s important to make sure you have the right hardware and software structures. In this guide, you’ll learn how to install your own Ubuntu FTP server and what specifics you should pay attention to.
Do you want to save or transfer data? Then rent a secure FTP Hosting from IONOS. Secure transfers via SSH and SSL/TLS, as well as daily back-ups are included.
Installing an Ubuntu FTP server
Before you can begin setting up your own FTP server, you have to find the appropriate software. For this, Ubuntu systems already have their own package management solution vsftpd, which you just need to install. The open source application for unix-like systems is built on modules and components characterised by particularly compact programming. In this way, vsftpd servers guarantee an excellent security standard and a stable performance, even with a high number of client accesses. To install the application, simply call the terminal and enter the following command:
sudo apt-get install vsftpdUbuntu FTP server tutorial: Configuration
After finishing the short installation, you can close the terminal again and start configuring the Ubuntu FTP server. To do this, open the configuration file vsftpd.conf, usually found in the ‘etc’ folder.
To be able to open and edit the configuration file of the FTP server, you need a simple text editor. Ubuntu has the program gedit (GNOME-Editor) preinstalled for this purpose, so that you don’t necessarily have to look for your own solution. The text content is divided into two sections: Lines that begin with the pound sign (#) are ignored by the vsftpd server. These lines are used to comment on different settings as well as deactivated functions. Lines that don’t begin with the pound sign, however, contain information that is interpreted later by the server.
There are no general requirements for additional setup of the FTP server, since it depends on what you personally need and what demands you place on your server. Here it’s important that you consider the various options first. In the following sections of this Ubuntu FTP server guide, you’ll find information about the various settings and their functions.
To save changes to the vsftpd.conf file, you need root permissions. Otherwise you can only read the configuration file.
Allow anonymous access
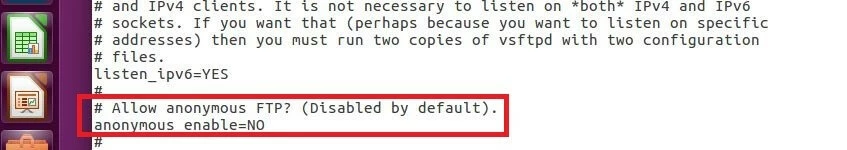
By default, vsftpd is configured so that users can log on to the FTP server only with a specific account. But the file transfer protocol allows for a login procedure where users can log in anonymously without having to provide personal data. To activate this unspecified access type, search for the entry ‘anonymous_enable=NO’ and change the ‘NO’ parameter to ‘YES’:
anonymous_enable=YESExtend anonymous user rights
By default, rights are extremely restricted for users who log in to an Ubuntu FTP server anonymously. For example, it’s only possible to download files that are readable by all users (anon_world_readable_only=YES). If you leave this statement out, then it’s possible to download other files too. The following options are available:
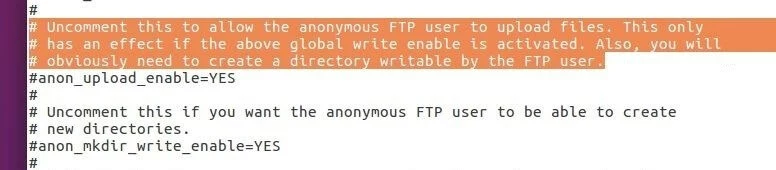
- anon_mkdir_write_enable: Anonymous users can create new directories if the value ‘YES’ is entered here. One additional requirement is that write_enable is activated (see the ‘Allow changes to the file system’ section below). Default value: ‘NO’ or deactivated (#) ‘YES’.
- anon_other_write_enable: If this line is activated, files and directories on the FTP server can also be renamed and deleted with anonymous access. Default value: ‘NO’ or deactivated (#) ‘YES’.
- anon_upload_enable: With this text line, the anonymous upload of files is activated. Requirements are that write_enable is activated and a separate upload directory is created, since anonymous users can’t write directly in the home directory. Default value: ‘NO’ or deactivated (#) ‘YES’.
If the FTP server is linked to the internet, it’s generally not recommended to extend the rights of anonymous users. This puts you at risk of your server being misused by a third party.
Restrict access to local users
If you only want to give local users access to their home directory /home/username, you can set this in the vsftpd.conf file. The markup parameter responsible for this is ‘chroot_local_user’, which is assigned the default value of ‘NO’. If you change the entry as follows
chroot_local_user=YESthen all other directories remain closed to local users.
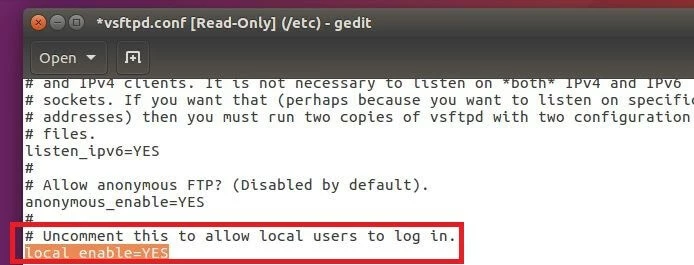
Disable local user login
To allow access to the FTP server for local users, the entry ‘local-enable=YES’ needs to be set – which it is under default settings. If you want to deny access to your Ubuntu FTP server for local users, you just need to comment out the corresponding line by placing a pound sign in front of it:
#local_enable=YESAllow changes to the file system
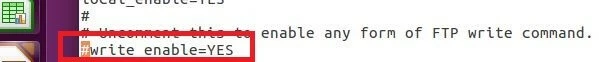
In the default configuration, it’s defined that neither local nor anonymous user can use FTP commands. The corresponding line for the global writing ‘#write_enable=YES’ is disabled. If a logged-in user should be allowed to customise the file system of the vsftpd server, then it’s necessary to extract the statement:
write_enable=YESLimit FTP access for particular users
In certain situations, it can be useful to deny FTP server access to certain users, or to clearly define which users can log in. For the first solution, add the following line to the end of the configuration file:
userlist_deny=YES
userlist_enable=YES
userlist_file=/etc/vsftpd.user_listThis parameter instructs the vsftpd server to deny access to all users listed in the external file vsftpd.user_list. In this case, all other users can log in as usual.
For the second scenario, where only users listed in vsftpd.user_list can log in, the parameter ‘userlist_deny”’ needs to be negated:
userlist_deny=NO
userlist_enable=YES
userlist_file=/etc/vsftpd.user_listIn both cases, it’s necessary to create the external text file and manually enter the specified users.
An overview of additional options
| Option | Default value | Description |
| download_enable | YES | Specifies whether downloads from the Ubuntu FTP server are possible |
| ssl_enable | NO | Offers the possibility to enable SSL encryption for FTP access |
| anon_max_rate | 0 | Sets the maximum transfer speed (bytes per second) for anonymous users; 0 stands for an unlimited rate |
| local_max_rate | 0 | Sets the maximum transfer speed (bytes per second) for local users; 0 stands for an unlimited rate |
| max_clients | 0 | Maximum value for the number of clients logged on to the FTP server at the same time; 0 means no restriction |
| anon_root | /home/ftp | Directory to which anonymous users are automatically sent |
| log_ftp_protocol | NO | Logs all FTP requests and responses |
| connect_timeout | 60 | Defines the time span (in seconds) after which the connection between the server and the client is interrupted in the absence of communication |
| ftpd_banner | Welcome text | |
| guest_enable | NO | Allows you to unblock the anonymous access profile defined in guest_username |
| guest_username | ftp | Username for anonymous login |
You can find a complete list of all options by using the following command in the terminal:
man vsftpd.confHow to use the FTP server under Ubuntu
After you’ve set the configuration file to your desired specifications, don’t forget to save it. For the server application to accept all changes, a restart is required, which you initiate with the following command:
sudo etc/init.d/vsftpd restartIf you haven’t started the FTP server yet, do this with the terminal command:
sudo etc/init.d/vsftpd startIf you want to stop the Ubuntu FTP server again, replace the ‘start’ parameter in the above command with ‘stop’.
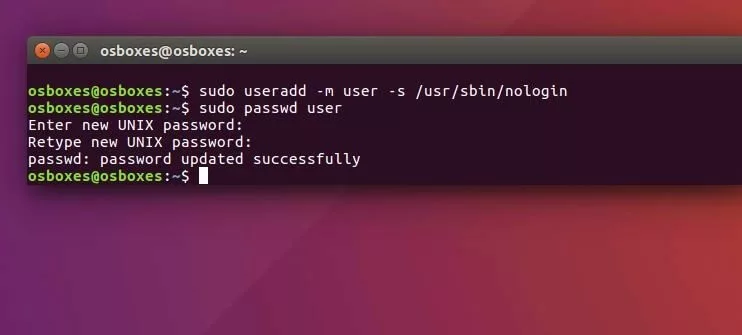
Now that you’ve installed your Ubuntu FTP server and started it, you need a user account to be able to log in. For this example, we created a user with the name ‘user’ and the password ‘password’.
sudo useradd -m user -s/usr/sbin/nologin
sudo passwd userYou now allow login access for the nologin shell by adding the following line to the end of the /etc/shells file:
/usr/sbin/nologinYou can now use the created user account to establish a connection to the vsftpd server with an FTP client. A popular solution that is standard with Ubuntu is the cross-platform open source application FileZilla. The installation works in the usual way via the terminal:
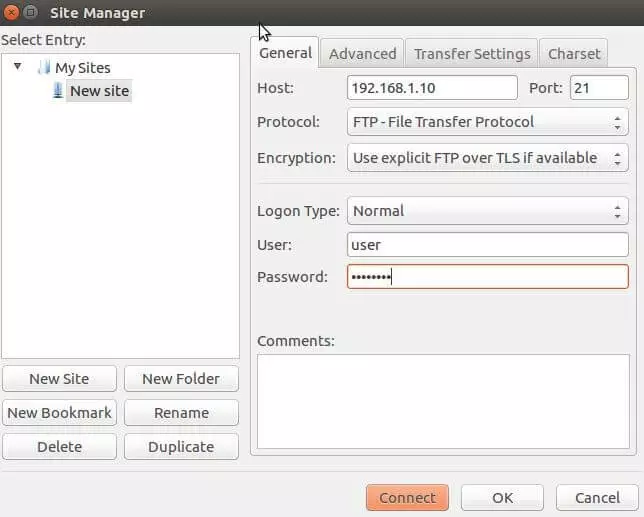
sudo apt-get install filezillaOpen FileZilla and add a new connection with the corresponding data: Under host, enter the IP address of your Ubuntu FTP server, which receives requests on port 21 (so long as you haven’t changed the settings). Select the file transfer protocol and, if possible, select SFTP (Secure FTP) or FTP over TLS, since a simple FTP connection via port 21 represents a relatively high security risk. In the ‘Logon Type’ field, select the ‘Normal’ option. For ‘User’ and ‘Password’, you need the previously created login data of the example account. By clicking on ‘Connect’, you join the server.
500 OOPS: Security feature takes care of problems
If you have installed an Ubuntu FTP server and certain settings aren’t working, there could be many underlying causes: It’s possible that you’ve forgotten to restart the FTP server, or to save the configuration file. Syntax errors can sneak into the vsftpd.conf file if, for example, a space is set in the wrong place. The following is a common error message with a completely different cause:
500 OOPS: vsftpd: refusing to run with writable root inside chroot ()This message, which can be encountered during the connection establishment, isn’t an error message, but instead a security feature. The cause is a possible vulnerability of the glibc library (Ubuntu standard library of the C programming language), which could be used for users to write their own root directory. Two solutions exist to avoid this security catch:
1. Remove write permission in the user’s root directory: Withdraw local users of writing rights for their own root directory, so that they can only write in subdirectories. The restriction solves the ‘500 OOPS’ problem, but this can become a disadvantage when files need to be written to the root directory. The terminal command for this approach is as follows:
chmod a-w /home/user2. Allow write permission for the root directory in the vsftpd.conf file: If you don’t have any security concerns about the abuse of writing rights, you can also inform the Ubuntu FTP server that this function is explicitly desired. For this, one additional entry is needed in the configuration file:
allow_writeable_chroot=YESTry out your VPS for 30 days. If you're not satisfied, we'll fully reimburse you.